2016 70-341 NEW Dumps is Released Today!
Exam Code: 70-341
Exam Name: Core Solutions of Microsoft Exchange Server 2013
Certification Provider: Microsoft
Corresponding Certifications: MCSE, MCSE: Messaging
2016 Skills will be tested in the 70-341 certification exam:
1.Install, configure, and manage the mailbox role
2.Plan, install, configure, and manage client access
3.Plan, install, configure, and manage transport
4.Design and manage an Exchange infrastructure
ATTENTION: 2016 New Added Questions will be a big difficulty!
Several 2016 NEW ADDED 70-341 Exam Questions:
QUESTION 201
You have an Exchange Server 2013 server named Server1.
Server1 has a single mailbox database named DB1.
You configure deleted items to be retained for 30 days.
You need to ensure that each item that passes the retention period is removed daily between 2:00 and 6:00.
What should you do?
A. Run the Set-RetentionPolicy cmdlet.
B. Run the Start-ManagedFolderAssistant cmdlet.
C. Modify the maintenance schedule for DB1.
D. Modify the messaging records management (MRM) schedule for Server1.
Answer: C
Explanation:
In the question it says nothing about a Retention policy.
To configure deleted items to be retained for 30 days we can do it on a database level, using this cmdlet:
Set-MailboxDatabase -Identity “DB1” -DeletedItemRetention 30.00:00:00
And after the above, configure the maintenance of DB1 using the Set-MailboxDatabase cmdlet with the – MaintenanceSchedule parameter.
QUESTION 202
You have an Exchange Server 2013 organization.
You need to create a resource record in DNS to support Autodiscover from the Internet.
What type of resource record should you create?
A. Host (A)
B. Text (TXT)
C. Pointer (PTR)
D. Mail exchange (MX)
Answer: A
QUESTION 203
You have an Active Directory forest named contoso.com.
You install a new Exchange Server 2013 organization that contains a Client Access server named CAS1.
You need to configure certificates in the organization to support the following client connections:
Autodiscover Outlook Anywhere Exchange ActiveSync
What should you do?
A. Reissue a self-signed certificate to CAS1.
B. Configure the default Web site on CAS1 to require SSL.
C. Issue a trusted certificate that contains multiple subject alternate names.
D. Install Active Directory Rights Management Service (AD RMS) on a member server.
Answer: C
QUESTION 204
You have an Exchange Server 2013 organization.
The organization is authoritative for the domain contoso.com.
You create a federated trust.
You need to ensure that federated partners can automatically locate the Client Access servers in the organization.
What should you create from an external DNS server?
A. an A record for autodiscover.contoso.com
B. an A record for FederatedSharing.contoso.com
C. an SRV record for _autodiscover._TCP._msdcs.contoso.com
D. an SRV record for _FederatedSharing._UDP._msdcs.contoso.com
Answer: A
Explanation:
As mentioned in another question, this should actually be a CNAME record, according to Technet, but I left this in here as an A record for contoso.com would need creating before the CNAME for autodiscover.contoso.com. The exam will only mention CNAME records though.
QUESTION 205
You have an Exchange Server organization.
The organization contains a server named EX01 that has Exchange Server 2010 installed and a server named EX02 that has Exchange Server 2013 installed.
Your mailbox is hosted on EX01.
You need to access the Exchange Admin Center (EAC).
Which URL should you use?
A. https://EX01/ecp?ExchClientVer= 14
B. https://EX02/ecp?ExchClientVer= 15
C. https://EX02/eac?ExchClientVer=15
D. https://EX01/ecp?ExchCfientVer=15
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/jj150562(v=exchg.150).aspx
If you’re in a coexistence scenario, where you’re running Exchange 2010 and Exchange 2013 in the same organization, and your mailbox is still housed on the Exchange 2010 Mailbox server, the browser will default to the Exchange 2010 ECP.
You can access the EAC by adding the Exchange version to the URL.
For example, to access the EAC whose virtual directory is hosted on the Client Access server CAS15-NA, use the following URL: https://CAS15-NA/ecp?ExchClientVer=15.
Conversely, if you want to access the Exchange 2010 ECP and your mailbox resides on an Exchange 2013 Mailbox server, use the following URL:
https://CAS14-NA/ecp?ExchClientVer=14.
QUESTION 206
Your network contains an Active Directory forest named contoso.com.
The forest contains the domain controllers configured as shown in the following table.

You plan to deploy an Exchange Server 2013 organization to the forest
A company policy prevents administrators from logging on to DC2 to perform installations.
You need to prepare the Active Directory schema for the planned Exchange Server deployment.
You verify that your user account has all the required permissions to achieve the task.
The solution must minimize changes to the Active Directory infrastructure.
A. Move the schema master role to DC1, and then run Exchange setup.
B. Deploy a member server to contoso.com, and then move the server to the West site.
Run adprep.exe from the member server.
C. Log on to DC3 and then run Exchange setup.
D. Log on to any server in the West site, and then run Exchange setup.
Answer: A
Explanation:
Prepare Active Directory and domains for Exchange 2013. The first step in getting your organization ready for Exchange 2013 is to extend the Active Directory schema.
Exchange stores a lot of information in Active Directory but before it can do that, it needs to add and update classes, attributes, and other items. Before you extend your schema, there are a few things to keep in mind:
* The only way to extend the schema for Exchange is to use Setup.exe in Windows Command Prompt or use Exchange 2013 Setup. Other ways of extending the schema aren’t supported.
* The computer where you’ll run the command to extend the schema needs to be in the same Active Directory domain and site as the schema master.
We can accomplish this be by moving the schema master role to DC, and then run Exchange setup.
Incorrect answers:
Not B: Adprep is used to upgrade the Active Directory infrastructure forest to a newer version such as to Windows Server 2008. Adprep is not used for Exchange Server infrastructure changes. Not C: Exchange Setup must be run from the Schema master. DC3 does not have the schema master role.
Not D: Only DC2 in the West site has the Schema master role.
We cannot run Exchange Setup from the other servers in the West site.
https://technet.microsoft.com/en-us/library/bb125224%28v=exchg.150%29.aspx
QUESTION 207
You have an Exchange Server 2013 organization.
A new policy requires that all iPhone users access their on-premises mailbox by using the OWA for iPhone app.
You need to ensure that push notifications for the OWA for iPhone app are configured before the users install the app.
Which three actions should you perform? Each correct answer presents part of the solution.
A. Configure Microsoft Azure Active Directory Sync (Azure AD Sync).
B. Modify the EWS virtual directory.
C. Enable push notifications proxy.
D. Enroll in Microsoft Office 365 for business.
E. Modify the OWA virtual directory.
F. Set up on premises Exchange 2013 to Office 365 Authentication.
Answer: CDF
Explanation:
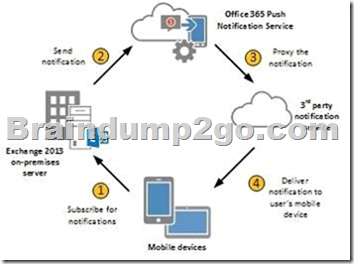
Configuring push notifications proxying for OWA for Devices
To enable push notifications, the admin must:
1. (D) Enroll your organization in Office 365 for business.
2. Update all on-premises servers to Exchange Server 2013 Cumulative Update 3 (CU3) or later.
3. (F) Set up On-premises Exchange 2013 to Office 365 Authentication
4. (C) Enable push notifications from the on-premises Exchange Server 2013 to Office 365 and verify that push notifications are working.
Illustration below:
Incorrect answers:
Not A: There is no need to configure Microsoft Azure Active Directory Sync.
Not B: You do not have to modify the EWS virtual directory.
Not E: You do not have to modify the OWAvirtual directory.
https://technet.microsoft.com/en-us/library/dn511017%28v=exchg.150%29.aspx
QUESTION 208
You have an Exchange Server 2010 organization.
You deploy several Exchange Server 2013 servers to the organization and you deploy the required certificates.
You attempt to connect to an Exchange Server 2013 server by using Outlook Web App and you discover the error message shown in the exhibit (Click the Exhibit button.)
Exhibit: * Missing*
You need to prevent the error message from appearing when users access Outlook Web App on the new servers.
What should you do?
A. Remove the Exchange Server 2010 servers from the organization.
B. Run the Remove-ExchangeCertificate cmdlet.
C. From the Exchange Management Console, remove the certificates from the Exchange Server
2010 servers.
D. From the Exchange Admin Center, modify the properties of the OWA virtual directory.
Answer: B
Explanation:
We remove the Exchange Server 2010 servers certificates.
The certificates are removed with the Remove- ExchangeCertificate cmdlet.
Note that the Exchange 2010 SSL certificate can be re-used if it contains the correct namespaces. You can export the SSL certificate from Exchange 2010 and import it into Exchange 2013. However, if the names on the certificate are not correct, or the certificate is due to expire soon anyway, you may find it easier to simply acquire a new SSL certificate.
Incorrect answers:
Not A: We must remove the certificate for the Exchange Server 2010 servers. If you just remove the Exchange Server 2010 servers the certificates for them would still cause problems.
Not C: We cannot remove the certificates from the Exchange Management Console.
Not D: Modifying the OWA virtual directory would not address the certificate problem.
https://technet.microsoft.com/en-us/library/aa997569%28v=exchg.150%29.aspx
QUESTION 209
A company named Contoso, Ltd. has an Exchange Server 2013 organization that contains two servers.
Contoso has a subsidiary named Fabrikam, Inc.
All users have mailboxes in the Contoso organization.
You implement an address book policy (ABP) for the users from Fabrikam.
A company policy states that the users from Contoso must not be able to view the contact cards of the Fabrikam users.
You need to implement a solution to meet the requirement of the company policy.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Run the New-TransportRule cmdlet
B. Modify the properties of the ABP.
C. Run the Set-TransportConfig cmdlet.
D. Run the Set-Mailbox cmdlet.
E. Install and Enable the Address Book Policy Routing agent.
F. Modify the properties of the global address list (GAL).
Answer: EF
Explanation:
F: First we modify the properties of GAL of the ABP so that only Fabrikam users can access the ABP.
An Address Book Policy consists of a subset of the various address objects that exist in the.
The resulting scope of an ABP is equal to that of the GAL contained in the policy, Note: Global address list (GAL) segmentation (also known as GAL segregation) is the process whereby administrators can segment users into specific populations to provide customized views of their organization’s GAL. Address book policies (ABPs) allow you to segment users into specific groups to provide customized views of your organization’s global address list (GAL). When creating an ABP, you assign a GAL, an offline address book (OAB), a room list, and one or more address lists to the policy. You can then assign the ABP to mailbox users, providing them with access to a customized GAL in Outlook and Outlook Web App. The goal is to provide a simpler mechanism to accomplish GAL segmentation for on- premises organizations that require multiple GALs. .
E: If you’re using ABPs, and you don’t want users in separate virtual organizations to view each other’s potentially private information, you can turn on the Address Book Policy Routing agent. The ABP Routing agent is a Transport agent that controls how recipients are resolved in your organization. When the ABP Routing agent is installed and configured, users that are assigned to different GALs appear as external recipients in that they can’t view external recipients’ contact cards.
Incorrect answers:
Not A: The New-TransportRule cmdlet is used to create transport rules in your organization, but transport rules does not affect the ABP.
Not B: The properties of the ABP would not affect which users can view contact information or not. This is decided by the GAL of the ABP.
Not C: The Set-TransportConfig cmdlet is used to modify the transport configuration settings for the whole Exchange organization, but it would not affect the ABP.
Not D: We can use the Set-Mailbox cmdlet with the AddressBookPolicy parameter to assign the ABP to users, but here the ABP is already implemented for the users (and we assume it has already been assigned to the users).
https://technet.microsoft.com/en-us/library/hh529948%28v=exchg.150%29.aspx
QUESTION 210
Your company has a main office and three branch offices.
You have an Exchange Server 2013 organization. The main office contains five Exchange servers. Each branch office contains two Exchange servers. All of the servers have all of the Exchange server roles installed. Each branch office contains one database availability group (DAG).
You need to recommend a load balancing solution for the branch offices. The solution must ensure that both servers in each office are the targets of all client connections.
What are two possible recommendations? Each correct answer presents a complete solution.
A. DNS round robin
B. Layer 4 hardware load balancers
C. CAS arrays
D. Network Load Balancing (NLB) clusters
Answer: BC
Explanation:
B: The use of hardware load balancers is still supported for Exchange 2013.
C: In Exchange 2010, Microsoft introduced the concept of a Client Access array.
After a Client Access array was configured for an Active Directory site, all Client Access servers in the site automatically became members of the array. In current builds of Exchange 2013, no configuration of a Client Access array is required, because the deployment of a load balanced and highly available service is much simpler.
Incorrect answers:
Not A: A: a DNS round robin could in theory be used entirely in place of a hardware load balancer – in fact it’s almost as effective as using Windows Network Load balancing.
However, DNS Round robin is in fact no load balancer.
Not D: Windows Network Load Balancing (WNLB) can’t be used on Exchange servers where mailbox DAGs are also being used because WNLB is incompatible with Windows failover clustering. If you’re using an Exchange 2013 DAG and you want to use WNLB, you need to have the Client Access server role and the Mailbox server role running on separate servers.
https://technet.microsoft.com/en-us/library/jj898588%28v=exchg.150%29.aspx
QUESTION 211
You have an Exchange Server 2013 organization named contoso.com that contains 10 servers. Your company purchases a company named Fabrikam, Inc. Fabrikam has an Exchange Server organization named fabrikam.com. All of the email messages sent between the organizations is routed over the Internet.
You need to ensure that the email messages sent from contoso.com to fabrikam.com are encrypted.
What is best way to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
A. Create a Send connector of type Partner.
B. Instruct all of the users in contoso.com to use SMIME.
C. Modify the Authentication settings for the Send connectors in contoso.com.
D. Create a federation trust between the organizations.
Answer: A
Explanation:
Create a Send connector to send email to a partner, with Transport Layer Security (TLS) applied If you want to ensure secure, encrypted communication with a partner, you can create a Send connector that is configured to enforce Transport Layer Security (TLS) for messages sent to a partner domain. TLS provides secure communication over the Internet.
See step 2 below.
1. In the EAC, navigate to Mail flow > Send connectors, and then click Add .
2. In the New send connector wizard, specify a name for the send connector and then select Partner for the Type. When you select Partner, the connector is configured to allow connections only to servers that authenticate with TLS certificates. Click Next.
3. Verify that MX record associated with recipient domain is selected, which specifies that the connector uses the domain name system (DNS) to route mail. Click Next.
4. Under Address space, click Add . In the Add domain window, make sure SMTP is listed as the Type. For Fully Qualified Domain Name (FQDN), enter the name of your partner domain.
Click Save.
5. For Source server, click Add . In the Select a server window, select a Mailbox server that will be used to send mail to the Internet via the Client Access server and click Add.
After you’ve selected the server, click Add . Click OK.
6. Click Finish.
Incorrect answers:
Not B: We should not depend on the users to set up encryption.
We can enforce by configuring the send connection partner setting.
Not C: The authentication setting is not used to set up encrypted e-mail.
Not D: A federation trust is used to share resources in a forest, not to enforce encryption of email.
https://technet.microsoft.com/en-us/library/jj657514%28v=exchg.150%29.aspx
QUESTION 212
You have an Exchange Server 2013 organization that contains two Edge Transport servers.
The Edge Transport servers are configured to perform recipient filtering.
You deploy a new Edge Transport server named Edge3.
You need to ensure that Edge3 performs recipient filtering.
What should you do?
A. Create a new Edge Subscription for Edge3.
B. Run the Set-TransportConfig cmdlet on Edge3.
C. Export the Edge Subscription from an existing Edge Transport server and import the Edge Subscription
to Edge3.
D. Run the ExportEdgeConfig.ps1 and the ImportEdgeConfig.ps1 scripts.
Answer: D
Explanation:
We copy the configuration from an existing Edge Transport server with the ExportEdgeConfig.ps1 script and apply to new server Edge3 with ImportEdgeConfig.ps1 script.
Note: Configure Edge Transport server using cloned configuration
You can use the provided Exchange Management Shell scripts (located in % ExchangeInstallPath %Scripts) to duplicate the configuration of an Edge Transport server.
This process is referred to as cloned configuration. Cloned configuration is the practice of deploying new Edge Transport servers based on configuration information from a previously configured source server. The configuration information from the previously configured source server is copied and exported to an XML file, which is then imported to the target server.
Two Shell scripts are used to perform cloned configuration tasks:
* ExportEdgeConfig.ps1 Exports all user-configured settings and data from an Edge Transport server and stores that data in an XML file.
* ImportEdgeConfig.ps1 During the validate configuration step, the ImportEdgeConfig.ps1 script checks the exported XML file to see whether the server-specific export settings are valid for the target server.
Incorrect answers:
Not A: We do not need to create a new Edge subscription.
Not B: The Set-TransportConfig cmdlet is used to modify the transport configuration settings for the whole Exchange organization, but we just to copy the configuration of an Edge Transport server.
Not C: There are no commands to export and import Edge subscriptions.
https://technet.microsoft.com/en-us/library/aa996008%28v=exchg.150%29.aspx
QUESTION 213
You have an Exchange Server 2013 on-premises organization and a Microsoft Office 365 tenant.
All mailboxes are hosted on-premises.
You need to implement an archiving solution for all users.
The solution must ensure that all mailbox content older than 18 months is moved to Personal Archives in Office 365.
What should you implement?
A. A default policy tag (DPT)
B. A retention policy
C. A personal tag
D. A retention policy tag (RPT)
E. A retention hold
Answer: B
Explanation:
To apply one or more retention tags to a mailbox, you must add them to a retention policy and then apply the policy to mailboxes.
In our case we would need a default policy tag and then add it to a retention policy.
Incorrect answers:
Not B: We cannot apply a Default policy tag (DPT) to a mailbox.
We would need to add it to a retention policy.
Note: DPT actions include:
* Move to archive
* Delete and allow recovery
* Permanently delete
Users can’t change DPTs applied to a mailbox.
Not C: Personal tags allow your users to determine how long an item should be retained, but we need to implement a solution for all users.
Not D: The available actions for Retention policy tag (RPT) are:
* Delete and allow recovery
* Permanently delete.
RPT have no archive action.
Not E: A retention hold is used to halt retention policy, but we should not halt retention. Reference: https://technet.microsoft.com/en-us/library/dd297955%28v=exchg.150%29.aspx
QUESTION 214
In Europe, your company has one main office and five branch offices.
In Asia, the company has one main office and five branch offices.
Each main office contains a data center.
The network contains an Active Directory forest.
The forest contains a single domain named contoso.com.
Each office is configured as an Active Directory site.
All client computers are joined to the domain.
You plan to deploy Exchange Server 2013 servers to both data centers.
You need to recommend a client connectivity solution that meets the following requirements:
Users who connect from the Internet must be configured automatically to connect to their mailbox by using Outlook Anywhere.
Users from the branch offices must use Outlook Anywhere to connect to the Client Access servers in their respective region.
What should you include in the recommendation?
A. A service connection point (SCP) in Active Directory and a host (A) record in the public DNS zone
B. A service location (SRV) record in the internal DNS zone and a service location (SRV) record in the
public DNS zone
C. A service connection point (SCP) in Active Directory and an inbound port rule for TCP 389
D. A service location (SRV) record in the public DNS zone and an inbound port rule for TCP
Answer: B
Explanation:
You must provide a host service (SRV) resource record in DNS for Outlook clients to discover the Autodiscover service by using DNS.
We should provide two SRV records, one for the internal DNS zone and one for the public DNS zone.
Incorrect answers:
Not A: Service Connection Points (SCPs) are objects in Active Directory that hold information about services, but SCP would not be useful for setting up Outlook Anywhere. Instead we need to configure the DNS.
Not C, not D: TCP port 389 is the LDAP protocol, but Outlook Anywhere does not use this port so there is no need for a port rule for it.
The Windows RPC over HTTP Proxy component, which Outlook Anywhere clients use to connect, wraps remote procedure calls (RPCs) with an HTTP layer.
This allows traffic to traverse network firewalls without requiring RPC ports to be opened.
https://social.technet.microsoft.com/forums/exchange/en-US/957873ea-ea46-468e-843e-fae939ee1b82/srv-records-to-enable-auto-discover-for-outlook-anywhere
QUESTION 215
Drag and Drop Question
You have an Exchange Server 2013 organization that contains a server named EX1.
The network contains two domain controllers named DC1 and DC2.
You plan to make changes to the Active Directory infrastructure and to remove DC2 from the network.
You need to verify whether EX1 writes Active Directory changes to DC2.
What command should you run? To answer, select the appropriate options in the answer area.
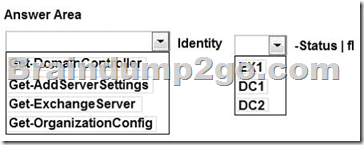
Answer:
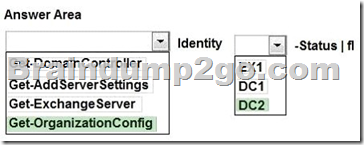
Explanation:
The Get-OrganizationConfig cmdlet is used to get configuration data for an Exchange organization.
We should specify DC2 as we are interested if information from EX1 is propagated to DC2. Example: This example gets the organization configuration information for the domain controller ContosoDC.
Get-OrganizationConfig -DomainController ContosoDC
Incorrect answers:
Not Get-ExchangeServer: The Get-ExchangeServer cmdlet is used to obtain the attributes of a specified Exchange server, but we are not interested in the attributes of EX1, we want to know if EX1 propagates changes to DC2.
Not Get-DomainController: The Get-DomainController cmdlet is used to view a list of domain controllers that exist in your organization, but we are interested in Active Directory information not a list of the Domain controllers.
Not Get-AddServerSettings: The Get-AdServerSettings cmdlet is used to view the Active Directory Domain Services (AD DS) environment settings in the current Windows PowerShell session, but we are not interested in PowerShell sessions.
https://technet.microsoft.com/en-us/library/aa997571%28v=exchg.150%29.aspx
QUESTION 216
Drag and Drop Question
You have an Exchange Server 2013 organization that contains the servers configured as shown in the following table.
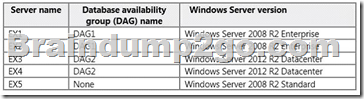
You need to add EX2 to DAG2. The solution must maintain redundancy for all mailbox databases.
Which five actions should you perform in sequence before you can add EX2 to DAG2? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
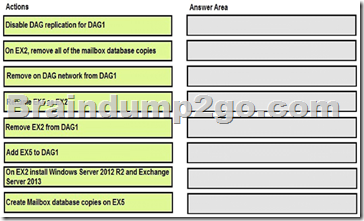
Answer:
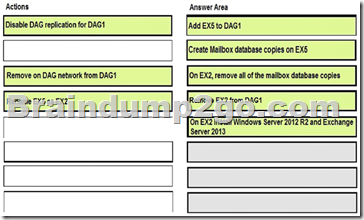
Explanation:
Box 1: Add EX5 to DAG1
We need to add EX5 to DAG1 for redundancy before we remove EX2.
Box 2: Create Mailbox database copies on EX5
We must set up EX5 mailbox database copies for redundancy before we remove EX2.
Box 3: On EX2, remove all of the mailbox database copies. We remove the DAG1 mailbox database copies from EX2. We must do this before removing EX2 from DAG1 as the Mailbox server must not host any replicated databases when it is removed.
Box 4: Remove EX2 from DAG1
Now can when EX5 being set up for DAG1 we can remove EX2 from DAG1. Box 5: On EX2 install Windows Server 2012 R2 and Exchange Server 2013 As the other members of DAG2 run Windows Server 2012 R2 datacenter we upgrade EX2 to Windows Server 2012 R2 as well.
Incorrect answers:
* There is no need to disable DAG replication for DAG1.
* There is no need to remove the DAG network from DAG1.
* Nothing would be accomplished by renaming EX5 to EX2.
https://technet.microsoft.com/en-us/library/dd297956%28v=exchg.150%29.aspx
QUESTION 217
Drag and Drop Question
You have an Exchange Server 2013 organization.
You need to recommend a solution to ensure that users can access their mailbox by using IMAP4.
The solution must meet the following requirements:
– The users must be able to download their email messages from multiple devices.
– The users must be able to look up their SMTP server from Outlook Web App.
– All IMAP4 connections must be audited.
What should you recommend? To answer drag the appropriate recommendation to the correct requirement. Each recommendation may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
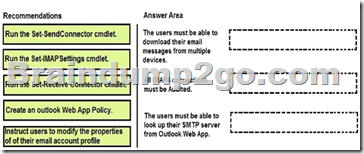
Answer:
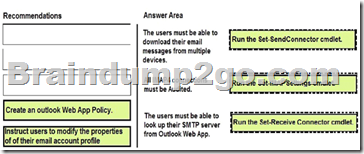
Explanation:
Box 1: Run the Set-SendConnector cmdlet.
In Microsoft Exchange Server 2013, a Send connector controls the flow of outbound messages to the receiving server. They are configured on Mailbox servers running the Transport service.
Most commonly, you configure a Send connector to send outbound email messages to a smart host or directly to their recipient, using DNS.
By default, Microsoft Exchange Server 2013 doesn’t allow you to send mail outside of your domain. To send mail outside your domain, you need to create a Send connector.
Box 2: You can set up logging with Set-IMAPSettings.
This example turns on IMAP4 protocol logging. It also changes the IMAP4 protocol logging directory to C:\Imap4Logging.
Set-ImapSettings -ProtocolLogEnabled $true -LogFileLocation “C:\Imap4Logging”.
Note: The Set-ImapSettings cmdlet is used to set specific IMAP4 settings for the server running Microsoft Exchange Server 2013 that has the Client Access server role installed and that’s running the Microsoft Exchange IMAP4 service.
Box 3: Run the Set-ReceiveConnector Settings cmdlet.
Exchange 2013 servers running the Transport service require Receive connectors to receive messages from the Internet, from email clients, and from other email servers. A Receive connector controls inbound connections to the Exchange organization.
Incorrect answers:
* A Web App Policy cannot be used to allow access their SMTP server from the Outlook Web app.
* We cannot rely on users to modify their email account profiles.
We need a centralized solution.
https://technet.microsoft.com/en-us/library/aa998252%28v=exchg.150%29.aspx
QUESTION 218
Drag and Drop Question
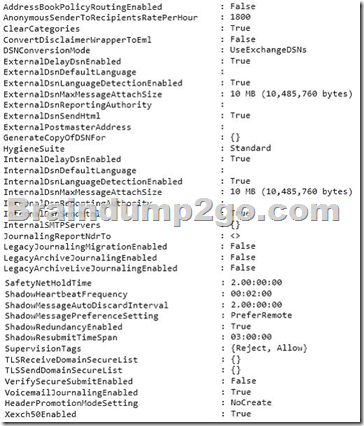
You have an Exchange Server 2013 organization that contains several servers in a single site. You run the Get-TransportConfig cmdlet and you receive the following output.
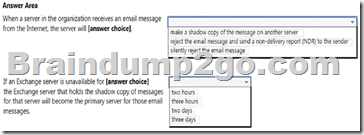
Use the drop-down menus to select the answer choice that completes each statement.
Answer:
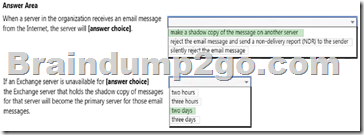
Explanation:
Box 1: make a shadow copy of the message on another server From the exhibit we see that: ShadowRedundacyEnable: True With shadow redundancy in Microsoft Exchange Server 2013 the transport server makes a redundant copy of any messages it receives before it acknowledges successfully receiving the message back to the sending server.
Box 2: two days
In the exhibit we see: ShadowMessageAutoDiscardInterval : 2.00:00:00 This means two days.
Note: Use the ShadowMessageAutoDiscardInterval parameter of the Set-TransportConfig cmdlet to configure the maximum age for shadow messages in your organization. By default, shadow messages are discarded automatically after two days.
This example reduces the retention period of shadow messages to four hours for your organization.
Set-TransportConfig -ShadowMessageAutoDiscardInterval 04:00:00
https://technet.microsoft.com/en-us/library/dd351027%28v=exchg.150%29.aspx
https://technet.microsoft.com/en-us/library/dd351046%28v=exchg.141%29.aspx
QUESTION 219
You have an Exchange Server 2013 organization.
Users connect to their mailbox by using Microsoft Outlook 2013 and mobile devices.
A user named User1 loses a mobile device.
You need to wipe the mobile device remotely.
Which cmdlet should you use?
A. Remove-MobileDevice
B. Clear-MobileDevice
C. Set-Mailbox
D. Remove-ActiveSyncDevice
Answer: B
Explanation:
The Clear-MobileDevice cmdlet deletes all user data from a mobile device the next time that the device receives data from the server running Microsoft Exchange Server 2013.
Incorrect answers:
Not A: The Remove-MobileDevice cmdlet is used to remove the mobile device partnership information that you specify from a user’s mobile device list stored in a mailbox on a computer running Microsoft Exchange Server 2013, but we don’t just want to remove the partnership information. We want wipe the device.
Not C: The Set-Mailbox cmdlet is used to modify the settings of an existing mailbox, but we need to wipe the mobile device.
Not D: The Remove-ActiveSyncDevice cmdlet is used to remove the mobile device partnership information that you specify from a user’s mobile device list stored in a mailbox on a computer running Microsoft Exchange Server 2013, , but we don’t just want to remove the device partnership information. We want wipe the device.
https://technet.microsoft.com/en-us/library/jj218658%28v=exchg.150%29.aspx
QUESTION 220
You verify that one email message sent to one mailboxes on EX1 are delivered successfully.
You also verify that all of mailbox databases on EX1 are mounted. Delete 20 GB of unnecessary data on EX1.
You discover that the hard disk drive on EX1 has only 10 GB of free space.
You delete 20 GB of unnecessary data on EX1. Users report that now they are receiving all of their email messages successfully to their mailbox.
You need to ensure that EX1 will prevent the delivery of email messages to mailboxes only if less than 2 GB of hard disk space is available.
What should you do?
A. Modify the Organization transport settings.
B. Disable the Safety Net feature.
C. Modify the EdgeTransportexe.config file.
D. Modify the mailbox database settings.
Answer: D
QUESTION 221
Hotspot Question
You have an Exchange Server 2013 organization. Each data center contains several Exchange servers and connects directly to the Internet. Each office has a Send connector to the Internet.
You configure each office as a separate site and you configure Main1 as a hub site.
The company opens a branch office that contains a small data center.
You deploy an Exchange Server 2013 server to the data center. The data center has a direct network link to Main1.
All of the site link costs are set to the default values.
In the table below identify through which office the email message will be transmitted first for each scenario.
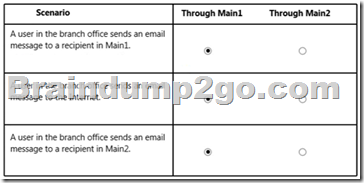
Answer: Pending
QUESTION 222
You have an Exchange Server 2013 organization that contains three Client Access servers named EX1, EX2, and EX3. The organization also contains eight Mailbox servers.
All users have client computers that have Microsoft Outlook 2013 installed.
You create a Network Load Balancing (NLB) cluster and add all of the Client Access servers as hosts in the cluster. The cluster has the following configurations:
– The default host is set to EX1.
– A port rule is configured for HTTPS traffic.
– The port rule has the affinity parameter set to Single.
– The port rule has the filtering mode set to Single host.
The port rule has the Handling priority set to the default option.
You discover that Outlook always connects to EX1.
You need to ensure that client connection are handled by all three Client Access servers.
What should you modify?
A. the filtering mode of the port rule.
B. the affinity parameter of the port rule.
C. the handling priority of the port rule.
D. the default host of the cluster.
Answer: C
QUESTION 223
Hotspot Question
You have an Exchange Server 2013 organization.
You deploy an Office Web Apps Server named Serverl.
You need to integrate the Office Web Apps Server and the Exchange Server organization.
What command should you run? To answer, select the appropriate options in the answer area.

Answer: Pending
QUESTION 224
Hotspot Question
Server1, Server2 and Server3 will be members of a database availability group (DAG) named DAG1.
You deploy a firewall between the internal network and the Internet.
You need to recommend a solution to meet the following requirements:
– Ensure that users can access their mailbox from the Internet by using Microsoft Outlook if a server fails.
– Ensure that users can access Unified Messaging (UM) services from the Internet if a server fails.
– Minimize costs.
What should you recommend? To answer, select the appropriate options in the answer area.
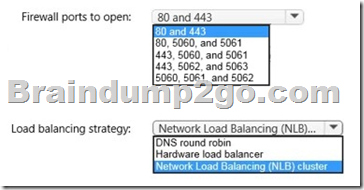
Answer: Pending
QUESTION 225
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. EX1 and EX2 are members of a database availability group (DAG) named DAG1.
Your organization contains several managed availability overrides.
Both EX1 and EX2 have a copy of a mailbox database named MBX1. MBX1 is active on EX1.
You discover that MBX1 on EX2 has a status of ServiceDown.
You need to restore the status of MBX1 on EX2 to healthy as quickly as possible.
What should you do?
A. Start the Microsoft Exchange Mail Replication Service.
B. Run Start-Service MSExchangelS.
C. Run Start-Service MSExchangeRepl.
D. Start the Microsoft Exchange DAG Management Service.
Answer: C
QUESTION 226
Hotspot Question
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. EX1 and EX2 are members of a database availability group (DAG) named DAG1.
You need to identify the last several times that a mailbox database named MBX1 failed over from EX1 to EX2.
What command should you run? To answer, select the appropriate options in the answer area.

Answer: Pending
2016 NEW 70-341 Dumps PDF & 70-341 Exam Questions 226Q Full Version Free Shared By Braindump2go: http://www.braindump2go.com/70-341.html