2016 NEW Cisco CCNP Security 300-208 SISAS Exam Questions Released Today!
Exam Code: 300-208
Exam Name: Implementing Cisco Secure Access Solutions (SISAS)
Certification Provider: Cisco
Corresponding Certification: CCNP Security
Introduction:
The Implementing Cisco Secure Access Solutions (SISAS) (300-208) exam tests whether a network security engineer knows the components and architecture of secure access. This 90-minute exam consists of 65–75 questions and assesses knowledge of Cisco Identity Services Engine (ISE) architecture, solution, and components as an overall network threat mitigation and endpoint control solutions. 300-208 exam also includes the fundamental concepts of bring your own device (BYOD) using posture and profiling services of ISE.
2016 NEW 300-208 Study Guides:
1. Identity Management/Secure Access
2. Threat Defense
3. Troubleshooting, Monitoring and Reporting Tools
4. Threat Defense Architectures
5. Identity Management Architectures
QUESTION 195
Which devices support download of environmental data and IP from Cisco ISE to SGT bindings in their SGFW implementation?
A. Cisco ASA devices
B. Cisco ISR G2 and later devices with ZBFW
C. Cisco ISR G3 devices with ZBFW
D. Cisco ASR devices with ZBFW
Answer: A
QUESTION 196
In Cisco ISE 1.3, where is BYOD enabled with dual-SSID onboarding?
A. client provisioning policy
B. client provisioning resources
C. BYOD portal
D. guest portal
Answer: D
QUESTION 197
Which description of the purpose of the Continue option in an authentication policy rule is true?
A. It allows Cisco ISE to check the list of rules in an authentication policy until there is a match.
B. It sends an authentication to the next subrule within the same authentication rule.
C. It allows Cisco ISE to proceed to the authorization policy regardless of authentication pass/fail.
D. It sends an authentication to the selected identity store.
E. It causes Cisco ISE to ignore the NAD because NAD will treat the Cisco ISE server as dead.
Answer: C
QUESTION 198
How many days does Cisco ISE wait before it purges a session from the active session list if no RADIUS Accounting STOP message is received?
A. 1
B. 5
C. 10
D. 15
Answer: B
QUESTION 199
A user configured a Cisco Identity Service Engine and switch to work with downloadable access list for wired dot1x users, though it is failing to work. Which command must be added to address the issue?
A. ip dhcp snooping
B. ip device tracking
C. dot1x pae authenticator
D. aaa authentication dot1x default group radius
Answer: B
QUESTION 200
Which option is the correct format of username in MAB authentication?
A. host/LSB67.cisco.com
B. [email protected]
C. 10:41:7F:46:9F:89
D. CISCO\chris
Answer: C
QUESTION 201
Refer to the exhibit. In a distributed deployment of Cisco ISE, which column in Figure 1 is used to fill in the Host Name field in Figure 2 to collect captures on Cisco ISE while authenticating the specific endpoint?
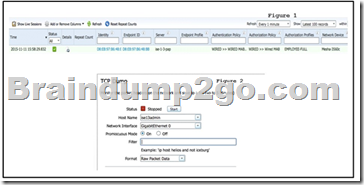
A. Server
B. Network Device
C. Endpoint ID
D. Identity
Answer: A
QUESTION 202
Which ISE feature is used to facilitate a BYOD deployment?
A. self-service personal device registration and onboarding
B. Guest Service Sponsor Portal
C. Local Web Auth
D. Guest Identity Source Sequence
Answer: A
QUESTION 203
What are two actions that can occur when an 802.1X-enabled port enters violation mode? (Choose two.)
A. The port is error disabled.
B. The port drops packets from any new device that sends traffic to the port.
C. The port generates a port resistance error.
D. The port attempts to repair the violation.
E. The port is placed in quarantine state.
F. The port is prevented from authenticating indefinitely.
Answer: AB
QUESTION 204
Which option describes the purpose of configuring Native Supplicant Profile on the Cisco ISE?
A. It helps employees add and manage new devices by entering the MAC address for the device.
B. It is used to register personal devices on the network.
C. It enforces the use of MSCHAPv2 or EAP-TLS for 802.1X authentication.
D. It provides posture assessments and remediation for devices that are attempting to gain access to the corporate network.
Answer: C
QUESTION 205
Which configuration is required in the Cisco ISE Authentication policy to allow Central Web Authentication?
A. Dot1x and if authentication failed continue
B. MAB and if user not found continue
C. MAB and if authentication failed continue
D. Dot1x and if user not found continue
Answer: B
2016 NEW 300-208 SISAS Questions and Answers 232q Full Version:http://www.braindump2go.com/300-208.html