MICROSOFT OFFICIAL: New Updated 70-410 Exam Questions from Braindump2go 70-410 pdf dumps and 70-410 vce dumps! Welcome to download the newest Braindump2go 70-410 vce&pdf dumps: http://www.braindump2go.com/70-410.html (471 Q&As)
Try 2015 Latet Updated 70-410 Practice Exam Questions and Answers, Pass 70-410 Actual Test 100% in 2015 New Year! Braindump2go Latest released Free Sample 70-410 Exam Questions are shared for instant download! Braindump2go holds the confidence of 70-410 exam candiates with Microsoft Official Guaranteed 70-410 Exa Dumps Products! 471 New Updated Questions and Answers! 2015 Microsoft 70-410 100% Success!
Exam Code: 70-410
Exam Name Installing and Configuring Windows Server 2012
Certification Provider: Microsoft
Corresponding Certifications: MCSA, MCSA: Windows Server 2012, MCSE, MCSE: Desktop Infrastructure, MCSE: Private Cloud, MCSE: Server Infrastructure
Keywords:70-410 Dumps,70-410 Exam Questions,70-410 VCE,70-410 VCE Free,70-410 PDF,70-410 Lab Manual PDF,70-410 Practice Exams,70-410 Practice Tests,70-410 Installing and Configuring Windows Server 2012
QUESTION 351
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have just executed the Uninstall-WindowsFeature Server-Gui-Shell L2P.com server, named L2P-SR13.
Which of the following is the reason for doing this?
A. To only remove Windows Explorer from L2P-SR13.
B. To only remove the Windows Internet Explorer from L2P-SR13.
C. To only remove the components and files related to Windows Explorer from L2PSR13.
D. To remove Windows Explorer, Windows Internet Explorer, and all associated components and files from
L2P-SR13.
Answer: D
Explanation:
Minimal Server Interface
If the server has a full installation of Windows Server, and I need to bring the server down to minimal server interface, I only need to remove the Server-GUI-Shell. The command is shown here.
Get-WindowsFeature Server-Gui-Shell | Uninstall-WindowsFeature – restart
Minimal Server Interface is situated between the Server Core and Server with a GUI modes, you can either install features on Server Core or remove features from Server with a GUI to reach the Minimal Server Interface installation state
http://blogs.technet.com/b/heyscriptingguy/archive/2013/01/25/use-powershell-to-remove-the-gui-on- windows-server-2012.aspx
http://blogs.technet.com/b/server_core/archive/2012/05/09/configuring-the-minimal-server-interface.aspx
QUESTION 352
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have been instructed to add a new domain controller to L2P.com’s existing environment.
Which of the following actions should you take?
A. You should consider making use of Server Manager.
B. You should consider making use of Authorization Manager.
C. You should consider making use of Remote Desktop Gateway Manager.
D. You should consider making use of Network Load Balancing Manager.
Answer: A
Explanation:
http://social.technet.microsoft.com/wiki/contents/articles/12370.step-by-step-guide-for-setting-up-windows- server-2012-domain-controller.aspx
QUESTION 353
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 installed.
You have been instructed to modify an Active Directory computer object.
Which of the following actions should you take?
A. You should consider making use of the Get-ADComputer Windows PowerShell cmdlet.
B. You should consider making use of the Set-ADComputer Windows PowerShell cmdlet
C. You should consider making use of the New-ADComputer Windows PowerShell cmdlet
D. You should consider making use of the Get-ADComputerServiceAccount Windows PowerShell cmdlet
Answer: B
Explanation:
Set-ADComputer – Modifies an Active Directory computer object.
http://technet.microsoft.com/en-us/library/ee617263.aspx
QUESTION 354
You work as an administrator at L2P.com. The L2P.com network consists of an Active Directory forest that contains a root domain, named L2P.com, and two child domains, named us.L2P.com and uk.L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
The root domain hosts a domain local distribution group, named L2PGroup.
You are preparing to issue L2PGroup read-only access to a shared folder hosted by the us.L2P.com domain.
You want to make sure that L2PGroup is able to access the shared folder in the us.L2P.com domain.
Which of the following actions should you take?
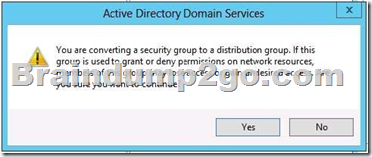
A. You should consider re-configuring L2PGroup as a universal Admins group.
B. You should consider re-configuring L2PGroup as a universal security group.
C. You should consider re-configuring L2PGroup as a global administrators group.
D. You should consider re-configuring L2PGroup as a local administrators group.
Answer: B
Explanation:
Group scope Universal can be assigned permissions in any domain or forest.
http://technet.microsoft.com/en-us/library/cc781446(v=ws.10).aspx http://technet.microsoft.com/en-us/library/cc755692(v=ws.10).aspx
QUESTION 355
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com.
L2P.com has a domain controller, named L2P-DC01, which has Windows Server 2012 R2 installed. Another L2P.com domain controller, named L2P-DC02, has Windows Server 2008 R2 installed.
You have deployed a server, named L2P-SR15, on L2P.com’s perimeter network. L2PSR15 is running a Server Core Installation of Windows Server 2012 R2.
You have been instructed to make sure that L2P-SR15 is part of the L2P.com domain.
Which of the following actions should you take?
A. You should consider making use of Set-Computer Windows PowerShell cmdlet on L2P-SR15.
B. You should consider making use of Get-Computer Windows PowerShell cmdlet on L2P-SR15.
C. You should consider making use of Test-Computer Windows PowerShell cmdlet on L2P-SR15.
D. You should consider making use of Add-Computer Windows PowerShell cmdlet on L2P-SR15.
Answer: D
Explanation:
Add-Computer – Add the local computer to a domain or workgroup.
http://technet.microsoft.com/en-us/library/hh849798.aspx
QUESTION 356
You work as an administrator at L2P.com. The L2P.com network consists of two Active Directory forests, named L2P.com and test.com. There is no trust relationship configured between the forests.
A backup of Group Policy object (GPO) from the test.com domain is stored on a domain controller in the L2P.com domain. You are informed that a GPO must be created in the L2P.com domain, and must be based on the settings of the GPO in the test.com domain.
You start by creating the new GPO using the New-GPO Windows PowerShell cmdlet. You want to complete the task via a Windows PowerShell cmdlet.
Which of the following actions should you take?
A. You should consider making use of the Invoke-GPUpdate Windows PowerShell cmdlet.
B. You should consider making use of the Copy-GPO Windows PowerShell cmdlet.
C. You should consider making use of the New-GPLink Windows PowerShell cmdlet.
D. You should consider making use of the Import-GPO Windows PowerShell cmdlet.
Answer: D
Explanation:
Import-GPO -Imports the Group Policy settings from a backed-up GPO into a specified GPO.
http://technet.microsoft.com/en-us/library/ee461044.aspx
QUESTION 357
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a server, named L2P-SR15, which is configured as a file server.
You have received instructions to make sure that a user, named Mia Hamm, has the ability to generate a complete backup of L2P-SR15 via Windows Server Backup.
Which of the following actions should you take?
A. You should consider making use of Computer Management to configure the local groups.
B. You should consider making use of Computer Management to configure the domain local groups.
C. You should consider making use of Computer Management to configure the global groups.
D. You should consider making use of Computer Management to configure the administrator groups.
Answer: A
Explanation:
To perform backups or recoveries by using Windows Server Backup, you must be a member of the Administrators or Backup Operators groups.
http://technet.microsoft.com/en-us/library/ee849849%28v=ws.10%29.aspx
Notes
You can only use Backup locally; you cannot backup a remote computer.
You can only back up and restore System State data on a local computer.
You cannot back up and restore System State data on a remote computer even if you are an administrator on the remote computer.
http://technet.microsoft.com/en-us/library/cc776822%28v=ws.10%29.aspx
QUESTION 358
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing the Windows Firewall with Advanced Security feature.
Which of the following is TRUE with regards to Windows Firewall with Advanced Security? (Choose all that apply.)
A. It provides host-based, two-way network traffic filtering for a computer.
B. It provides host-based, one-way network traffic filtering for a computer.
C. It blocks unauthorized network traffic flowing into or out of the local computer.
D. It only blocks unauthorized network traffic flowing into the local computer.
E. It only blocks unauthorized network traffic flowing out of the local computer.
Answer: AC
Explanation:
Windows Firewall with Advanced Security is an important part of a layered security model.
By providing host-based, two-way network traffic filtering for a computer, Windows Firewall with Advanced Security blocks unauthorized network traffic flowing into or out of the local computer. Windows Firewall with Advanced Security also works with Network Awareness so that it can apply security settings appropriate to the types of networks to which the computer is connected. Windows Firewall and Internet Protocol Security (IPsec) configuration settings are integrated into a single Microsoft Management Console (MMC) named portant part of your network’s
Windows Firewall with Advanced Security, so Windows Firewall is also an im isolation strategy.
http://technet.microsoft.com/en-us/library/hh831365.aspx
QUESTION 359
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing connection security rules.
Which of the following is TRUE with regards to connection security rules? (Choose all that apply.)
A. Connection security rules allows for traffic to be secured via IPsec.
B. Connection security rules do not allow the traffic through the firewall.
C. Connection security rules are applied to programs or services.
D. Connection security rules are applied between two computers.
Answer: ABD
Explanation:
Connection security involves the authentication of two computers before they begin communications and the securing of information sent between two computers. Windows Firewall with Advanced Security uses Internet Protocol security (IPsec) to achieve connection security by using key exchange, authentication, data integrity, and, optionally, data encryption.
How firewall rules and connection security rules are related
Firewall rules allow traffic through the firewall, but do not secure that traffic. To secure traffic with IPsec, you can create Computer Connection Security rules. However, the creation of a connection securityrule does not allow the traffic through the firewall. You must create a firewall rule to do this, if the traffic is not allowed by the default behavior of the firewall. Connection security rules are not applied toprograms or services; they are applied between the computers that make up the two endpoints.
http://technet.microsoft.com/en-us/library/cc772017.aspx
http://technet.microsoft.com/en-us/library/cc772017%28v=ws.10%29.aspx
QUESTION 360
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have been instructed to make sure that L2P.com users are not able to install a Windows Store application. You then create a rule for packaged apps.
Which of the following is the rule based on? (Choose all that apply.)
A. The publisher of the package.
B. The publisher of the application.
C. The name of the package
D. The name of the application
E. The package version.
F. The application version.
Answer: ACE
Explanation:
Packaged apps (also known as Windows 8 apps) are new to Windows Server 2012 R2 and Windows 8.
They are based on the new app model that ensures that all the files within an app package share the same identity. Therefore, it is possible to control the entire application using a single AppLocker rule as opposed to the non-packaged apps where each file within the app could have a unique identity. Windows does not support unsigned packaged apps which implies all packaged apps must be signed.
AppLocker supports only publisher rules for Packaged apps.
A publisher rule for a Packaged app is based on the following information:
Publisher of the package
Package name
Package version
All the files within a package as well as the package installer share these attributes. Therefore, an AppLocker rule for a Packaged app controls both the installation as well as the running of the app. Otherwise, the publisher rules for Packaged apps are no different than the rest of the rule collections; they support exceptions, can be increased or decreased in scope, and can be assigned to users and groups.
http://technet.microsoft.com/en-us/library/hh994588.aspx
Braindump2go Guarantee:
Pass-Certification 70-410 offers absolute risk free investment opportunity, values your timr and money! Braindump2go latest 70-410 Real Exam Dumps – Your success in 70-410 Exam is certain! Your belief in our 70-410 Exam Dumps is further strengthened with 100% Money Back Promise from Braindump2go!
70-410 PDF Dumps & 70-410 VCE Dumps Full Version Download(471q): http://www.braindump2go.com/70-410.html